What is Privileged Access Management (PAM) in Linux?
Linux Privileged Access Management (PAM) is a security practice that aims to control and manage access to privileged accounts and resources. In cybersecurity, protecting sensitive data and critical systems from unauthorized access is of utmost importance. Linux privileged access management is designed to protect these sensitive data and system resources by implementing strict controls over privileged accounts and ensuring only authorized personnel have access to them.
Privileges and How to Create Them?
In Linux, privileges are special rights granted to users and processes that allow them to perform certain operations that cannot be performed by regular users. These privileges can include,
- Access to sensitive files and resources.
- Modifying system-level configurations.
- Administrative tasks.
Sensitive File Privileges:
Linux uses a three-digit numeric code to represent file permissions, where each digit corresponds to a specific permission type:
- The first digit represents the owner's permissions.
- The second digit represents the group's permissions.
- The third digit represents everyone else's permissions.
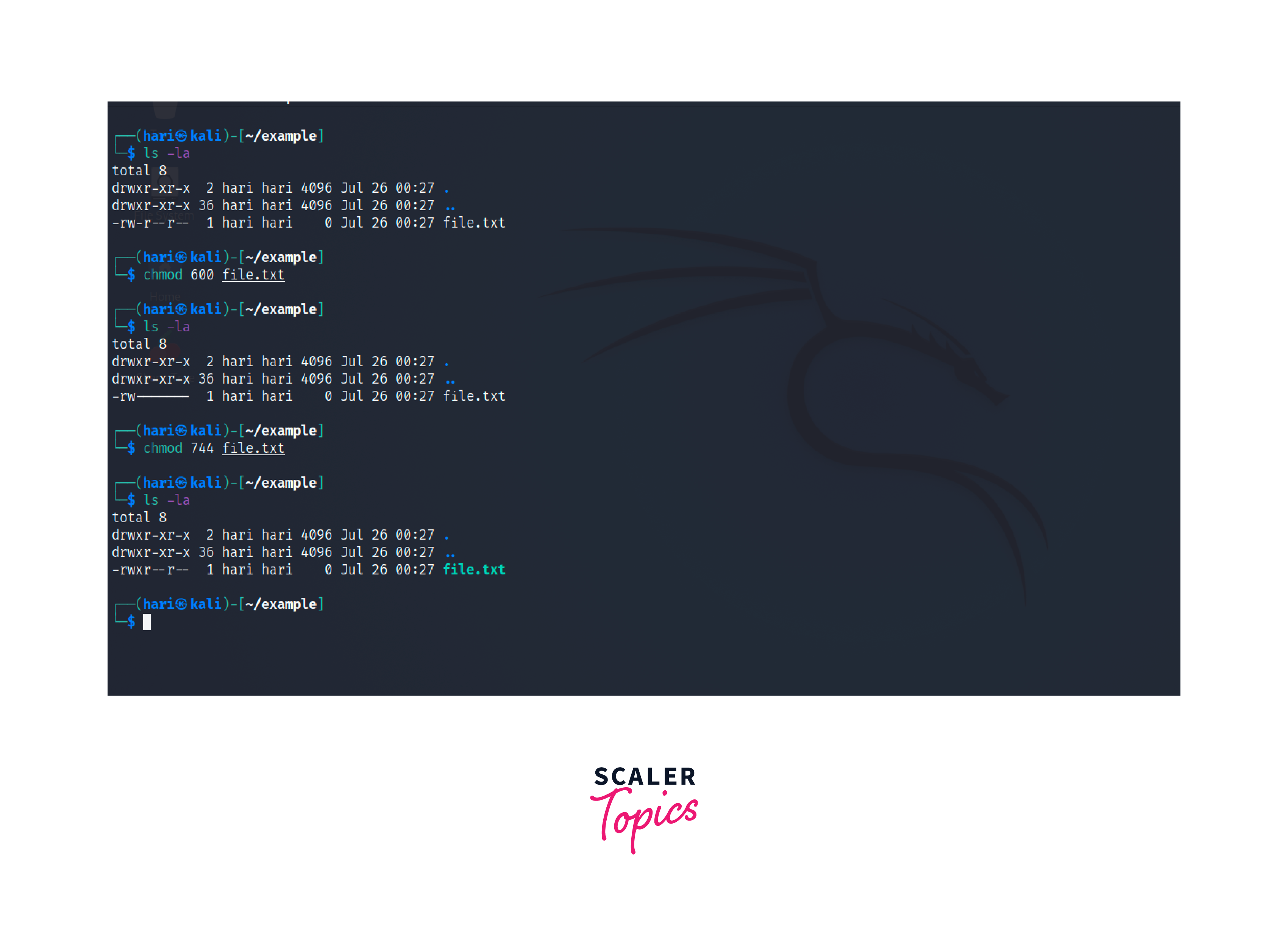
Each digit is composed of three bits: read (4) , write (2) , and execute (1) . To grant particular permission, add the corresponding values. For privileged access management Linux, you need to modify the file or directory permissions using the chmod command.
Syntax:
Example
- To grant read and write permissions to the file.txt for the owner only, we can use the following command,
We use 6 as the sum of read and write permissions numbers(4 + 2 = 6). The 0 will not affect the privileges of groups and others.
- To grant read, write and execute permissions to the owner, and read-only permissions to the group and others:
Superuser Privileges:
Certain operations, like installing software or modifying system files, require superuser (root) privileges. To execute commands with root privileges, use the sudo command. When using sudo , you'll be prompted to enter your password to confirm your identity before the command is executed. This is part of Privileged access management Linux.
Syntax:
Example: To edit a system configuration such as the ssh configuration file with root privileges:

Custom Privileges:
The /etc/sudoers file is a configuration file in Linux that controls the privileged access management linux for users and groups such as,
The /etc/sudoers file is edited using the visudo command, which ensures that only one person can edit it at a time and checks for syntax errors before saving changes. Syntax:
- user_or_group : Specifies the user or group to whom the rule applies.
- host : Defines the host or machine where the rule is in effect. It is usually set to ALL , to be valid on all hosts.
- runas_user : Specifies the user as whom the command will be run. If not specified, it defaults to the root user.
- command : Denotes the commands that the user or group is allowed to run with sudo privileges.
Example:
Let's say we have a user named, bob who needs to be able to restart the Apache web server without entering his password. To achieve this, we will add an entry for bob in the /etc/sudoers file.
- Open the /etc/sudoers file using the visudo command:
- Add the following line to the end of the file:
This specifies that Bob can run the Apache service using the sudo command without entering any password on the system.
We can also create groups with specified Linux-privileged access management and add users to the group.
Why do We Need PAM?
Privileged Access Management Linux (PAM) is essential in Linux environments for several critical reasons:
- Serves as a robust security layer** that protects sensitive data and critical systems from unauthorized access.
- Help mitigate the risk of security breaches and data leaks by implementing strict access controls and monitoring privileged user activities.
- Reduces the risk of misuse of privileges by limiting access to only authorized users.
- Offer monitoring and auditing capabilities that enable real-time tracking of privileged user activities.
- Allows temporary privilege elevation, to perform specific tasks.
- Secure password management by enforcing password complexity, expiring passwords regularly, and supporting password rotation policies.
- Helps organizations meet industry regulations** and security standards by maintaining a detailed audit trail of privileged activities.
Benefits of PAM
Linux-privileged access management offers several significant benefits, including:
- Help mitigate the risk of security breaches and data leaks.
- Reduces the attack surface for potential cyber threats by controlling privileged access.
- Centralized management of privileged access across the entire Linux infrastructure.
- Flexible to the specific needs of an organization, allowing administrators to fine-tune access policies according to their requirements.
- Reduces the risk of Malware infection by strictly limiting access to only authorized users or processes. As malware requires more privileges, it can't affect the system.
What is a Privileged Account?
In Linux privileged access management, a privileged account refers to a user account with administrative rights, also known as superuser or root. These accounts possess more privileges compared to regular users, enabling them to modify system configuration files, install software, and perform other critical tasks.
Types of Privileged Accounts
There are different types of privileged accounts, each with varying levels of access and responsibilities. These privileged accounts are used by many organizations and here are the typical types of privileged accounts:
- Root Account: Superuser account with the highest level of privileges on Privileged access management Linux. It has unrestricted access to all system resources, including critical configuration files and directories.
- Service Accounts: Created to run specific services or applications on a Linux system. These accounts are typically used for automated tasks or processes and may require elevated privileges.
- Administrative Accounts: Used by system administrators to manage and configure the Linux infrastructure. These accounts also have elevated privileges for tasks like installing software, modifying system settings, and managing users and groups.
- Emergency Accounts: Reserved for crises, such as when normal administrative accounts are unavailable or compromised.
- Application Accounts: Used by software applications and services to interact with the operating system and access specific resources. These accounts often require elevated privileges to perform their designated functions.
- Database Accounts: Used by database management systems (DBMS) to access and manage databases. These accounts require privileged access to perform tasks like database creation, modification, and backups.
- Backup and Recovery Accounts: Primarily for data backup and restoration purposes. Proper security measures, such as restricting access and regularly changing passwords, are crucial for these accounts.
What are Privileged Credentials?
In Linux privileged access management, privileged credentials refer to the authentication information and authorization credentials associated with privileged accounts. These accounts possess elevated privileges and permissions. Privileged credentials can be any of the following:
- Privileged accounts are typically protected by a combination of username and password
- SSH keys use cryptographic key pairs containing a private key and a public key for authentication. Privileged accounts often use SSH keys for secure remote access and automated processes.
- Certificates like X.509 digital certificates are used in public key infrastructure (PKI) environments to authenticate and verify the identity of users and systems.
- Some organizations also use biometric authentication methods such as fingerprint or iris scans for privileged accounts to ensure a higher level of security and prevent unauthorized access.
Privileged Thread Factors
When dealing with Linux-privileged access management, certain factors must be taken into account:
- Privileged Access Management Linux sessions should have time limits to reduce the exposure of sensitive activities.
- Real-time monitoring and recording of privileged sessions are crucial for auditing and forensics. Organizations can trace and investigate suspicious behavior through logs.
- Implementing multiple authentication layers like Multi-factor authentication (MFA) which requires users to provide multiple forms of identification before gaining access.
- Following the least privilege principle ensures that users have only the minimum level of access necessary to perform their duties which minimizes the attack surface and potential impact of a breach.
- Session isolation ensures that each privileged session runs in a separate, isolated environment to maintain data confidentiality and integrity.
- Protecting against privilege escalation attempts is vital to prevent attackers from gaining higher levels of access.
- Implementing Just-in-Time (JIT) privilege access allows users to acquire elevated privileges only when necessary for specific tasks.
- Implementing robust alerting mechanisms ensures that security teams are promptly notified of suspicious activities related to privileged accounts.
- Strong password policies for privileged accounts are essential. Regularly changing passwords and avoiding the use of default or weak credentials can prevent unauthorized access to critical systems.
- Employ secure authentication methods, such as cryptographic keys or certificates, for accessing privileged accounts. These methods provide higher levels of security compared to traditional methods.
PAM Best Practices
To effectively implement Linux-privileged access management, consider these best practices:
- Centralized Management: Use centralized PAM solutions to control access across the entire Linux infrastructure.
- Regular Access Reviews: Conduct regular access reviews to ensure privileges are up-to-date and aligned with organizational requirements.
- Strong Authentication: Enforce strong authentication mechanisms, such as multi-factor authentication (MFA) or cryptographic keys and certificate-based based authentication for privileged accounts.
- Continuous Monitoring: Employ real-time monitoring and alerting to detect suspicious activities and potential security breaches promptly.
- Segregation of Duties (SoD): SoD ensures that no single individual has complete control over critical operations which provides less risk.
- Least Privilege Principle: Apply the principle of least privilege, which grants users the minimum level of access required to perform their tasks.
- Credential Rotation: Regularly change privileged credentials, including passwords and SSH keys. This practice limits the exposure time in case of a security breach or unauthorized access.
- Secure Storage and Encryption: Privileged credentials should be securely stored and encrypted to prevent unauthorized access, even in the event of a data breach.
- Emergency Access Plan: Establish an emergency access plan for critical situations, such as when regular administrative access is unavailable.
Conclusion
- Privileged Access Management Linux (PAM) is a security practice that controls and manages access to privileged accounts and resources.
- PAM is necessary to protect sensitive data and critical systems from unauthorized access and cyber threats.
- Benefits of PAM include enhanced security, compliance adherence, monitoring capabilities, and reduced insider threats.
- Privileged accounts in Linux include root accounts, service accounts, administrative accounts, emergency accounts, application accounts, and database accounts.
- Privileged credentials are authentication information associated with privileged accounts, including usernames, passwords, SSH keys, and certificates.
- PAM best practices include centralized management, least privilege principle, multi-factor authentication, privilege elevation, and audit and monitoring.



